Frequently asked questions
Silent Armor’s AI engine models attacker behavior using global telemetry, MITRE ATT&CK mappings, and 0-day exploit data. By correlating signals from the dark web, external exposures, and network anomalies, it forecasts potential breach paths before exploitation occurs.
Silent Armor’s analytics engine fuses telemetry from DNS, SSL, endpoint, and cloud logs with dark-web and OSINT feeds. Using graph-based correlation, it identifies linked indicators - domains, IPs, credentials, and malware samples - to surface multi-stage or cross-vector attack campaigns in real time.
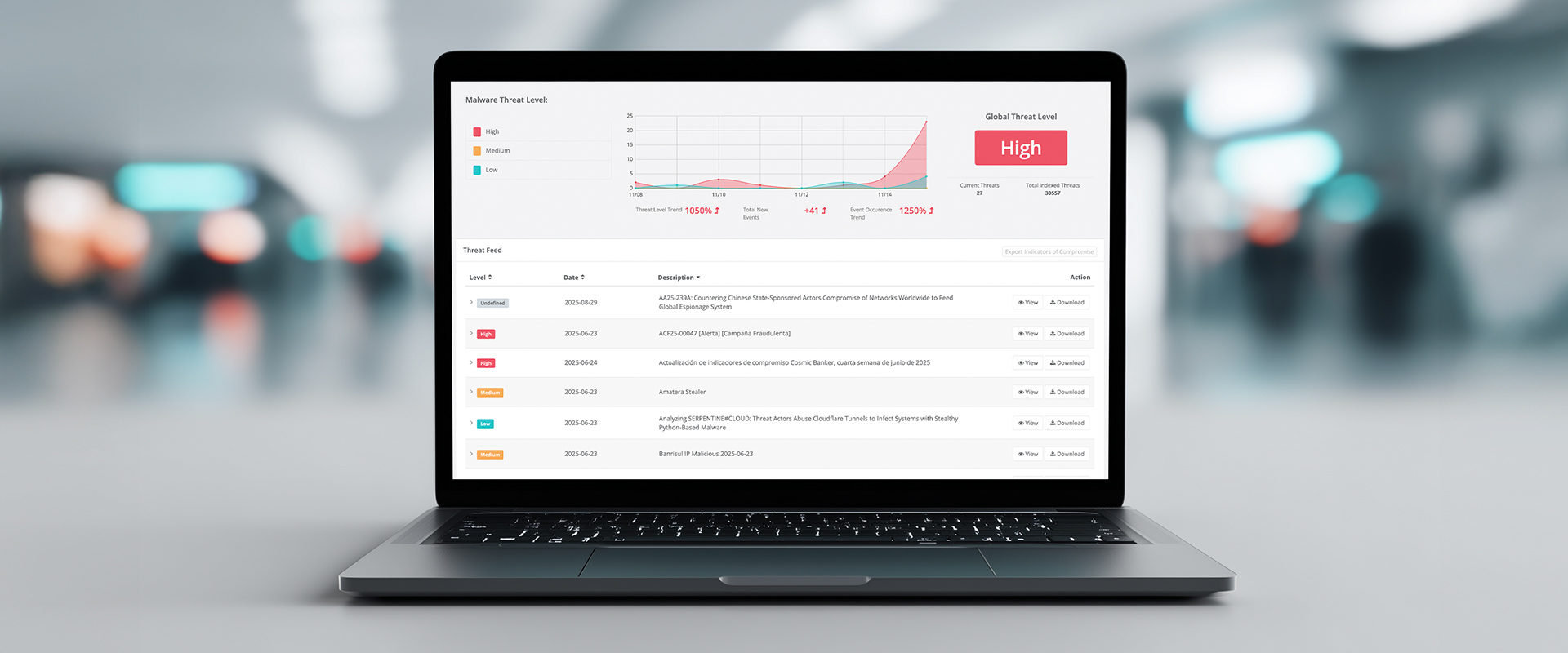
Silent Armor continuously ingests live threat feeds from dark-web marketplaces, malware repositories, and breach databases. Its intelligence graph updates in near real time to ensure coverage of newly emerging indicators and attacker infrastructure.
No. Silent Armor performs agentless monitoring by scanning external assets, analyzing DNS, SSL, and open ports, and correlating telemetry data. This reduces friction while maintaining complete visibility across your attack surface.
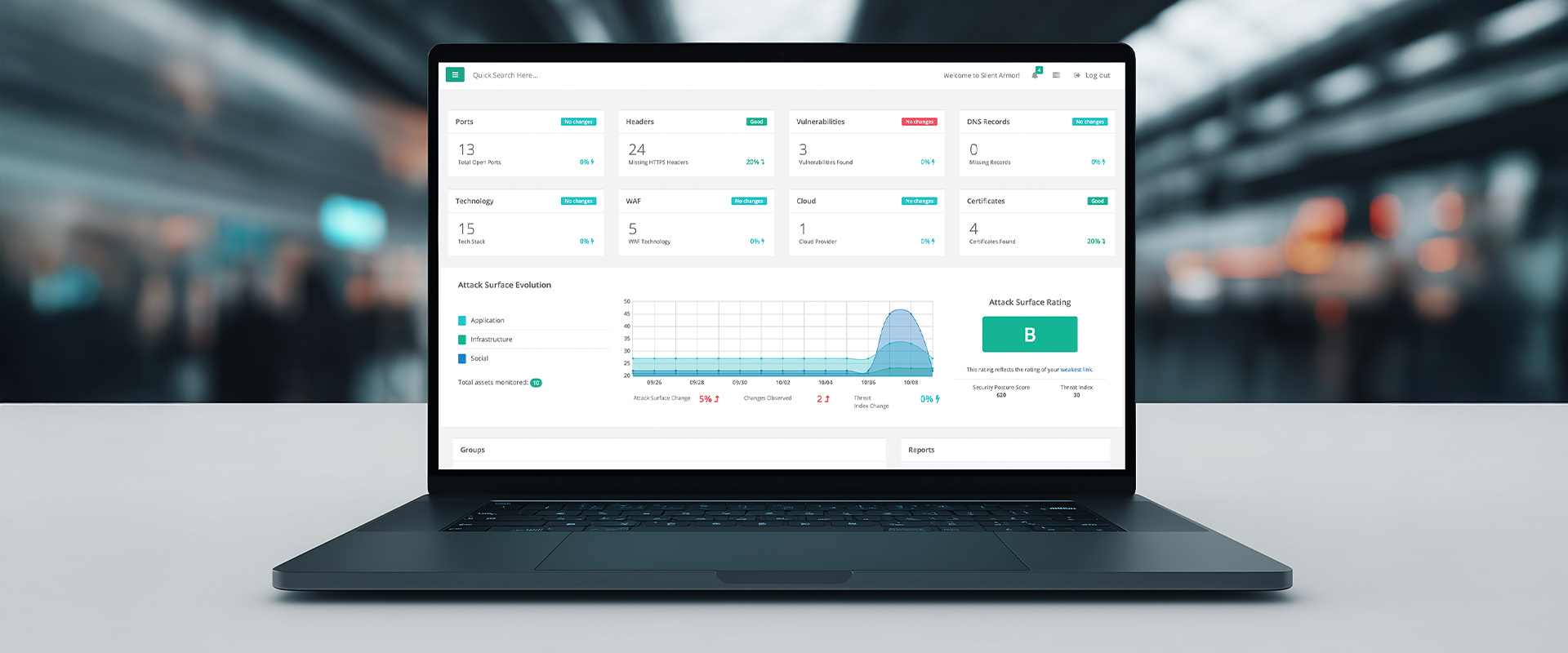
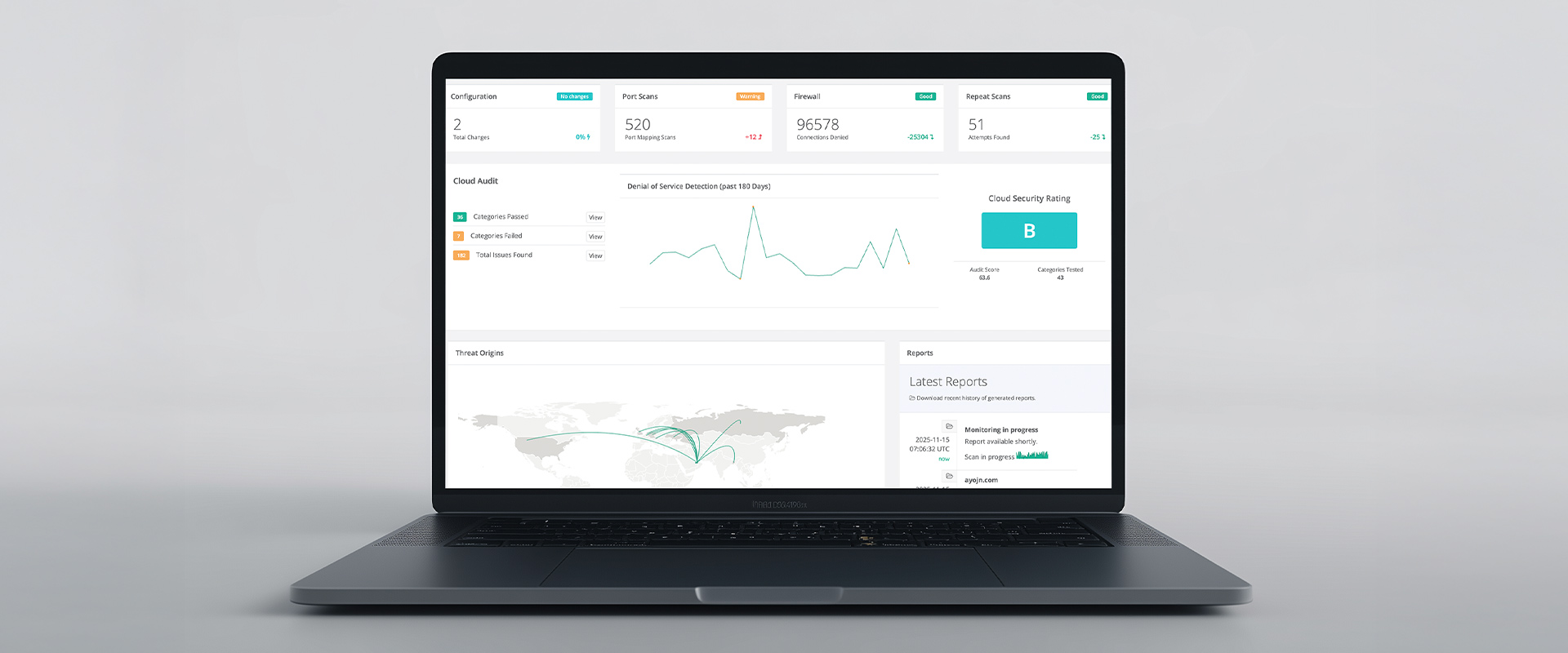
Users receive detailed exposure summaries, breach-likelihood scores, and remediation roadmaps. Reports can be customized for executive, compliance, or technical audiences and include visual threat maps and prioritized mitigation insights.
Silent Armor encrypts all collected telemetry using AES-256 and TLS 1.3 during transit and storage. Data processing follows strict role-based access controls and regional data residency options. The platform aligns with SOC 2, ISO 27001, and GDPR standards to ensure full regulatory compliance for enterprise clients.


.svg)